If you are searching about Securing Sensitive Data through AI and ML-Driven Cloud Models | i2tutorials you've visit to the right web. We...
If you are searching about Securing Sensitive Data through AI and ML-Driven Cloud Models | i2tutorials you've visit to the right web. We have 17 Pics about Securing Sensitive Data through AI and ML-Driven Cloud Models | i2tutorials like Securing Sensitive Data through AI and ML-Driven Cloud Models | i2tutorials, 8 Simple Steps to Revamp Your Cloud Data Security | Cloud computing and also Is Data Safe in the Cloud? | GlobalDots. Read more:
Securing Sensitive Data Through AI And ML-Driven Cloud Models | I2tutorials
 www.i2tutorials.com
www.i2tutorials.com securing cybersecurity wallarm microservices emea launches i2tutorials wise role booming segments industrywired webmagspace
Cloud Computer Vs. Traditional PC | Visual.ly
cloud vs computer traditional pc infographic technology computing between services science service tricks visual digital marketing visualistan difference data benefits
Edge Computing, Fog Computing, IoT, And Securing Them All
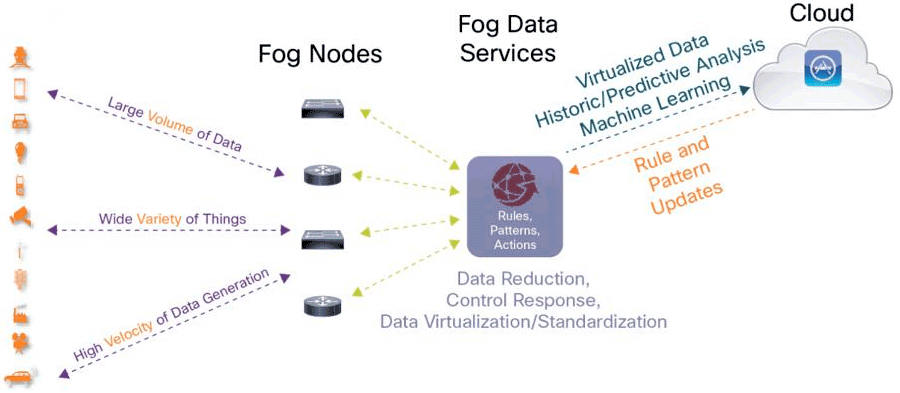 www.circleid.com
www.circleid.com fog securing solucionario materiales
Cloud Cryptography: What Is It And How Can You Benefit From It
 www.turningcloud.com
www.turningcloud.com cloud cryptography benefit
Is Data Safe In The Cloud? | GlobalDots
 www.globaldots.com
www.globaldots.com encryption practices
IBM Z15 Mainframe, Amps-up Cloud, Security Features | Network World
 www.networkworld.com
www.networkworld.com ibm z15
Secured Cloud Integration Services At Cost Effective Rates | HEX64
 www.hex64.net
www.hex64.net cloud integration services data security computing
Enhanced Security In Cloud Computing – A Traditional Approach In Modern
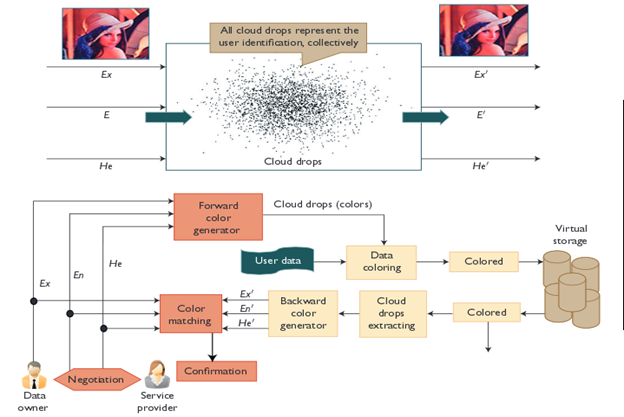 technophiliacsite.wordpress.com
technophiliacsite.wordpress.com integrity uphold
Securing The Internet Of Things (IoT) | OpenMind
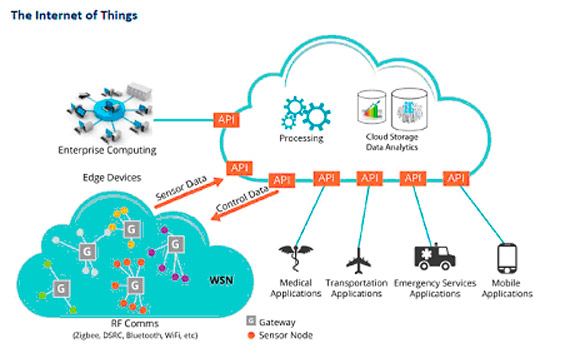 www.bbvaopenmind.com
www.bbvaopenmind.com iot things internet securing cloud computing openmind networks infrastructure
CLOUD COMPUTING SECURITY ISSUES, CHALLENGES AND SOLUTION - E2MATRIX
issues e2matrix dummies vulnerabilities
4 Ways Edge Computing Changes Your Threat Model | CSO Online
 www.csoonline.com
www.csoonline.com outsourcing verizon aws wavelength threat abbreviations metamorworks safevoip productif
Analyzing Security Threats To Virtual Machines Monitor In Cloud
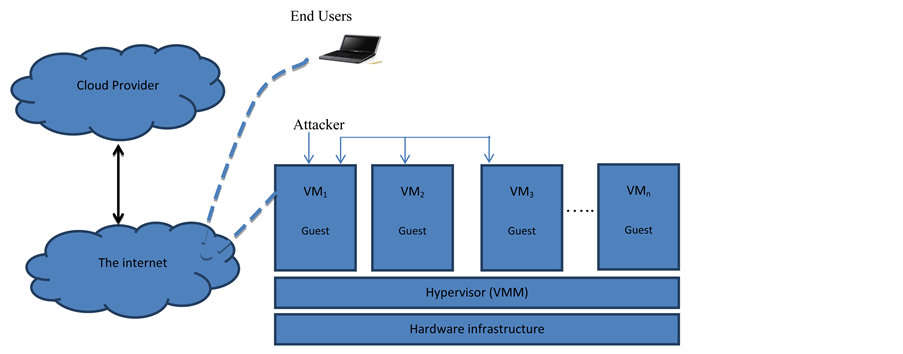 www.scirp.org
www.scirp.org vcci scirp
A220113
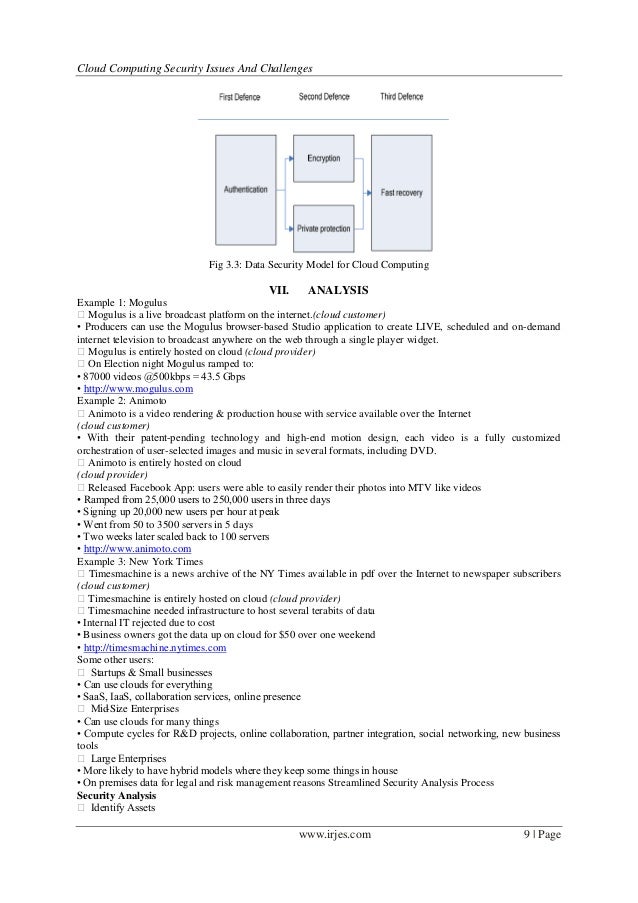 www.slideshare.net
www.slideshare.net Securing Data In The Cloud
 www.slideshare.net
www.slideshare.net Selecting A Security Framework | The Analysts
 www.theanalysts.co.uk
www.theanalysts.co.uk selecting
8 Simple Steps To Revamp Your Cloud Data Security | Cloud Computing
 in.pinterest.com
in.pinterest.com Cloud Computing Security From Single To Multicloud
 www.slideshare.net
www.slideshare.net multicloud
Cloud computing security issues, challenges and solution. Analyzing security threats to virtual machines monitor in cloud. Enhanced security in cloud computing – a traditional approach in modern




COMMENTS